Tuesday Topsight, August 15, 2006
 Today's Topsight Tuesday is all about things that worry and frighten us: massive asteroid impacts, terrorism, and Powerpoint.
Today's Topsight Tuesday is all about things that worry and frighten us: massive asteroid impacts, terrorism, and Powerpoint.
• Boom: This video at YouTube apparently comes from a Japanese program on global disasters. It shows what would happen if we had a major asteroid strike on Earth. And by "major," I mean "essentially hit by another planet" -- the asteroid in the video is far larger than anything that has struck the Earth since the earliest days of planetary formation. The asteroid shown is orders of magnitude larger than the one that hit the Earth at the end of the Cretaceous Period, wiping out the non-avian dinosaurs. It's quite literally a planet-killer.
Link to version on YouTube with great instrumental soundtrack. Link to version on YouTube with Japanese commentary.
The History Channel's "Mega-Disasters" series included a more likely scenario -- the impact of an asteroid a few miles in diameter. Los Angeles is obliterated in the show. The US History Channel doesn't have a repeat of this episode on the schedule, but it will show again in the UK -- and the UK site includes a preview video with some of the highlights.
• Smart Mob Security Concepts: Social networking pioneer Valdis Krebs has written a concise and readily-understood description of how social network analysis can be used to combat global guerillas. Connecting the Dots lays out how social network analysis works, and provides a real-world example using the 9/11 hijackers. Once suspects are identified, through traditional investigative/intelligence means, SNA takes over:
What do you do with these suspects? Arrest or deport them immediately? No, we need to use them to discover more of the al-Qaeda network. Once suspects have been discovered, we can use their daily activities to uncloak their network. Just like they used our technology against us, we can use their planning process against them. Watch them, and listen to their conversations to see...The structure of their extended network begins to emerge as data is discovered via surveillance.
- who they call / email
- who visits with them locally and in other cities
- where their money comes from
Not blanket, omnivorous surveillance, but targeted, narrow-but-deep surveillance, taking care to avoid guilt-by-association and looking for repeated patterns. Krebs underscores this point with an update about the recent UK capture:
It appears that this terror network was not disrupted by data mining of massive phone & financial records -- Big Brother was not involved. An entry point was found into the network, allowing the activity of the network to reveal the structure of the network -- all without bothering the other 60,000,000+ UK residents.
Counteracting terrorist/global guerilla groups through law enforcement tools and careful surveillance with warrants -- why didn't we think of that before?
(If you find this subject interesting, Krebs wrote a much longer and more detailed piece in early 2002 for First Monday, entitled Uncloaking Terrorist Networks.)
• Uses and Abuses of Powerpoint: Powerpoint is one of the necessary evils of the consulting world. Not necessary in the sense of being required to do your job well, but necessary in the sense of being required by many clients as an artifact of your work. It's entirely possible to construct useful and informative digital presentations (see, for example, Al Gore's Keynote deck in An Inconvenient Truth), but all too often these slideshows end up confusing more than illuminating.
Exhibit A, cited by Crooked Timber, in the wonderfully-titled Powerpoint Corrupts the Point Absolutely:
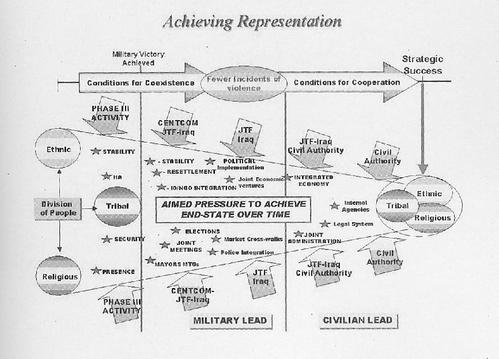
This is a slide from a Pentagon presentation on the reconstruction of Iraq, pulled from Thomas Ricks' book Fiasco. Setting aside the viability of the strategy, it's mind-boggling that anyone could think that this would be an enlightening construction of information.
My Powerpoint strategy? Pretty pictures, with a minimum of text, that underscore what I'm saying without distracting the audience.